Recently, the Sequoia-backed start-up Verkada suffered a major cyber-attack. In this event, a group of hackers claimed to have gained access to the live footage of 150,000 surveillance cameras from various locations, including jails, hospitals, gyms, companies, and schools.
Companies whose feeds were exposed include the electric car maker Tesla and cloud security provider Cloudflare. In addition, hackers got access to Verkada’s entire video archive of all of its customers. The hackers obtained access to 222 cameras in Tesla’s factories and warehouses.
Hackers gained access to Verkada through a “Super Admin” account, details of which were publicly exposed on the internet, allowing them to access all of its customers’ cameras. The hackers obtained the “root” access on the cameras, which enabled them to pivot and access the broader corporate network of Verkada’s customers or hijack the cameras and use them as a platform to launch future hacks.
IoT is going to be pervasive, so are the associated security concerns
Incidents like this reveal the lack of robust IoT security practices. Unstructured and fragmented security measures are a critical concern that impacts IoT’s reliability as an ecosystem. The issue around privacy and data leaks related to IoT devices and implementations is expected to rise as IoT adoption will further increase in the coming years. As per Globaldata’s ‘Emerging Technology Trends Survey’ of more than 1,700 senior executives worldwide, 59% of respondents are already investing in IoT, and 40% are expected to accelerate their IoT investment over the next 12 months.
Lack of IoT security can cause a significant risk for the business as well as to personal privacy
Business risk scenario: The big challenge for organizations trying to address IoT security is that most devices have weak or no security controls. Security cameras are an example of the sort of devices at risk. Apart from the recent Verkada incident, in 2016 the Mirai botnet attack targeted a variety of IoT and embedded devices, including IP cameras, routers, and printers, which impacted these devices with massive distributed denial-of-service (DDoS) attacks. The botnet infected nearly 65,000 IoT devices in its first 20 hours before reaching a steady-state population of between 200,000 and 300,000 infections.
Privacy risk scenario: In the Verkada surveillance breach, hackers got access to videos from women’s health clinics, psychiatric hospitals, schools and gyms, putting personal privacy at risk. Another similar incident was the Amazon Ring camera breach. In 2019, multiple families’ security systems were compromised. Hackers used the hacked cameras to invade people’s privacy and even demand ransoms.

US Tariffs are shifting - will you react or anticipate?
Don’t let policy changes catch you off guard. Stay proactive with real-time data and expert analysis.
By GlobalDataDue to the highly sensitive nature of the data produced by security cameras and other IoT devices, security remains the area with the highest perceived risk for IoT.
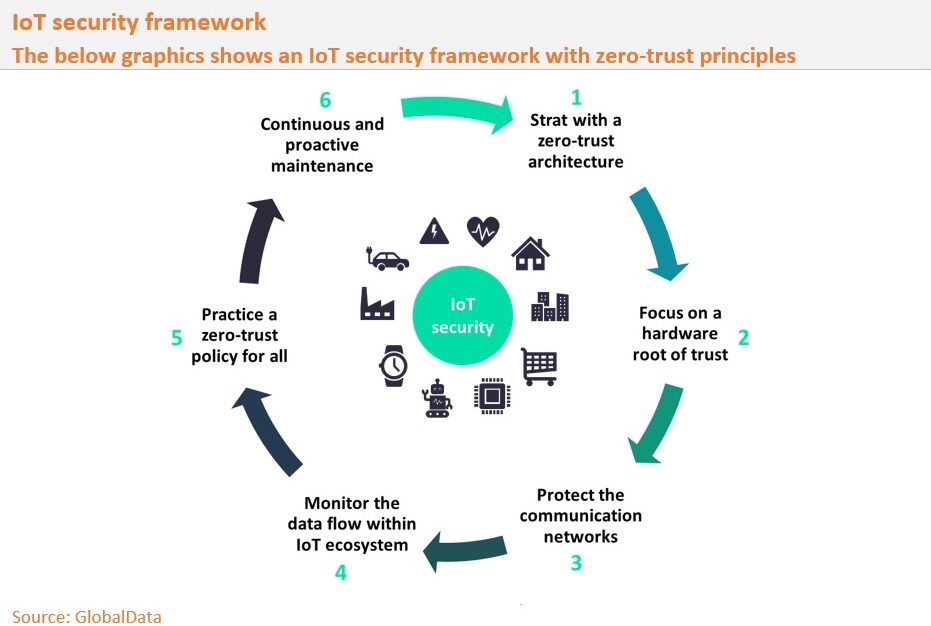
IoT security needs to be proactive, continuous, and collaborative
IoT at-risk devices include anything with an internet connection, from a refrigerator to smart locks, thermostats, lightbulbs, and vehicles. A significant threat is the prospect of attacks on sensors and devices used within the Industrial Internet or in smart cities domains. That is why organizations need to focus on a zero-trust principle, which should govern the IoT ecosystem’s design, development, and deployment. GlobalData suggests a six-step cyclic IoT security framework to combat IoT security issues, as shown in the below graphic.