
Twitter has been hit by what may be its worst hack in history, which saw attackers take control of some of the most high-profile verified accounts, including those owned by Elon Musk, Jeff Bezos, Barak Obama and Joe Biden.
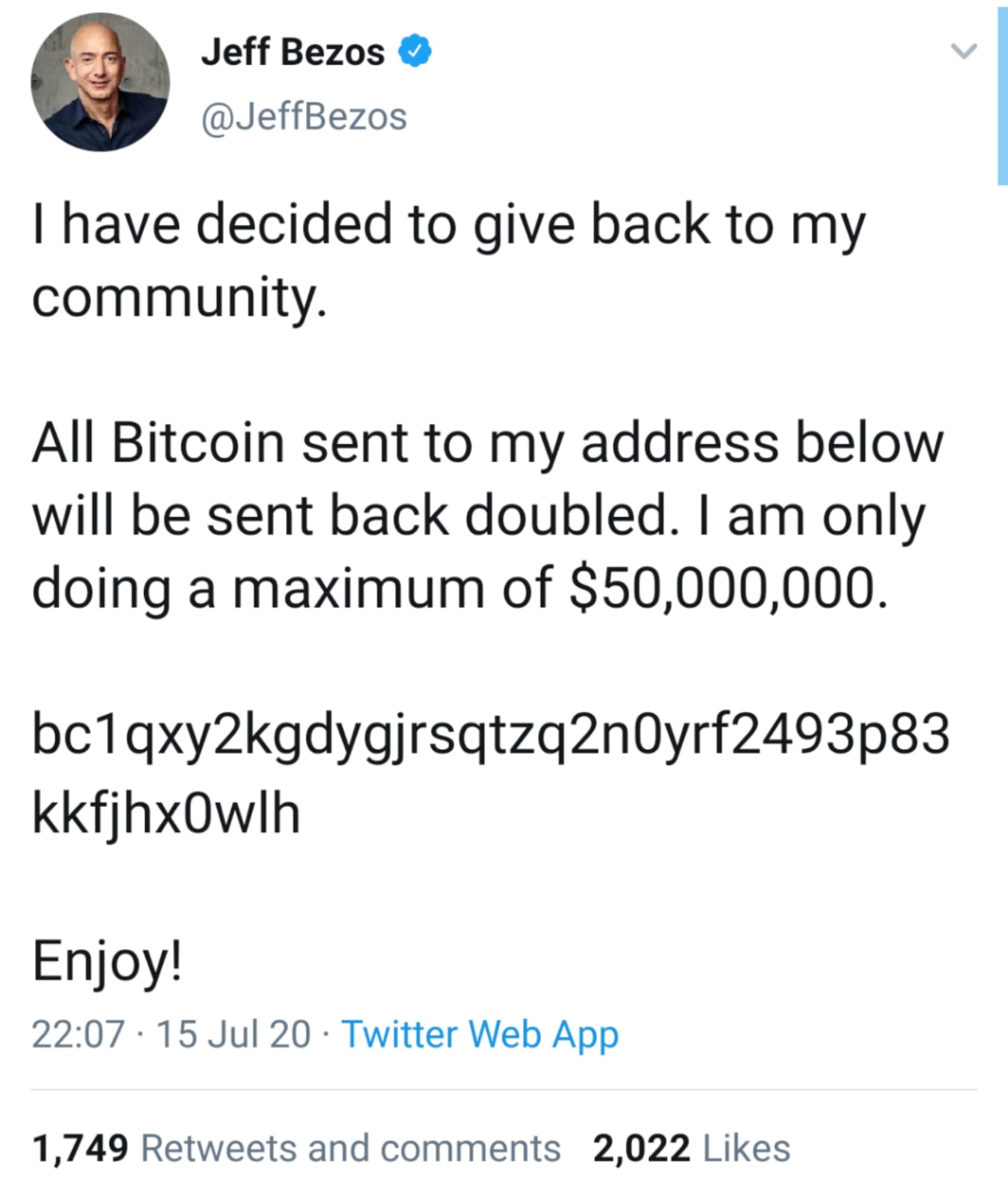
The attack began on Wednesday evening UK time, when a number of verified accounts – those with blue ticks – began tweeting variants of the same message. The phrase “I have decided to give back to my community”, or similar, followed by a call to send Bitcoin to a specific wallet address, on the promise that it would be “sent back doubled”.
Initially only a handful of verified accounts appeared to be impacted, including those of Microsoft founder Bill Gates and Tesla CEO Elon Musk. However, over the course of several hours, growing numbers of verified accounts were impacted.
These included a number of further key accounts in technology, including Amazon CEO Jeff Bezos and the official accounts of Apple and Uber, as well as key political figures including former president Barak Obama and US presidential candidate Joe Biden.
Celebrities such as Kanye West were also impacted, as were business giants including Berkshire Hathaway CEO Warren Buffett. In addition, key cryptocurrency and blockchain companies were affected, including Binance, Coinbase, Coindesk and Gemini.
 Twitter responds to hack, confirms inside access
Twitter responds to hack, confirms inside access
Twitter responded initially by saying it was “aware of a security incident” and locking down verified accounts’ ability to tweet. Meanwhile, the cybersecurity community argued that this was highly unlikely to be merely a coordinated attack on these accounts, but that hackers had likely gained access to a privileged admin account.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataHours later, Twitter Support provided an update, where it said its “investigation is still ongoing” but confirming these suspicions.
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools,” Twitter Support wrote.
“We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”
The fallout: Questions remain
While the attack has been quelled, the Bitcoin wallet the cryptocurrency was sent to shows that that large numbers of people did fall for the attack. Between 8pm and 11pm yesterday, the account received a total of $117,465.24 in Bitcoin, all but a hundred dollars of which has now been transferred to another account.
Meanwhile, efforts are now being made to determine how the attack was conducted – and how similar attacks can be prevented in the future. And some are calling for Twitter and the affected users to share details so that others in the cybersecurity community can help protect similar systems.
“For those accounts that were apparently compromised, it would be valuable if they could provide details on the method of attack,” said Tim Mackey, principal security strategist at the Synopsys Cybersecurity Research Centre.
“Doing so would allow everyone to ensure that the attack vector used can’t be successfully replicated again.”
For other cybersecurity experts, this is a sign that Twitter needs to re-think how it handles its superadmin accounts.
“Providing great customer support for high profile customers means IT administrators need privileged access to their accounts – to help reset passwords and to help clear up after an account takeover,” said Todd Peterson, IAM Evangelist at One Identity.
“However, with this great power comes great responsibility – and it takes only one bad admin to create global chaos by abusing their privileged access. Touching such high-profile Twitter accounts should be tied to an approval process, where a single person cannot act alone, without a detailed explanation and an approval by a superior.
“A modern record-and-review monitoring system would have also stopped the lone actor in their tracks by flagging the highly unusual activity and helping to retrace and undo their steps.”
There are also concerns that the level of access the hackers were able to gain has given the access to more than just the power to tweet to millions.
“If the hackers do have access to the backend of Twitter, or direct database access, there is nothing potentially stopping them from pilfering data in addition to using this tweet-scam as a distraction, albeit a very profitable one,” said Michael Borohovski, director of software engineering at Synopsys.
“We haven’t seen data on this, and won’t until a post-mortem is released by Twitter, but it’s a possibility.”
Read more: Trump is using Twitter to magnify his base: Anthony Scaramucci






