
A state-sponsored Russian home router hack in the UK and US has the potential to bring down national infrastructure, including air traffic control centres, experts have warned.
Over the last three years, hackers apparently enlisted by Russia have tried to seize control of the flow of worldwide internet traffic, according to an alert from the US Department of Homeland Security.
The attacks had the potential to paralyse airports, cripple government websites and electricity grids, as well as hack banking systems, Paul Hunton a cyber-security consultant at Hunton Woods, told Verdict:
The opportunities are fairly endless once you’ve got hold of the infrastructure.
You can target national infrastructure and air traffic control centres, potentially shutting down airports.
The alert marked the first time the UK and US have teamed up to issue a cyber-threat warning.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataSince 2015, Russia is understood to have methodically targeted ‘network infrastructure devices such as routers, switches, firewalls, network intrusion detection systems’, according to US and UK intelligence agencies.
The joint statement said:
The FBI has high confidence that Russian state-sponsored cyber actors are using compromised routers to conduct man-in-the-middle attacks to support espionage, extract intellectual property, maintain persistent access to victim networks, and potentially lay a foundation for future offensive operation.
How did the hack work?
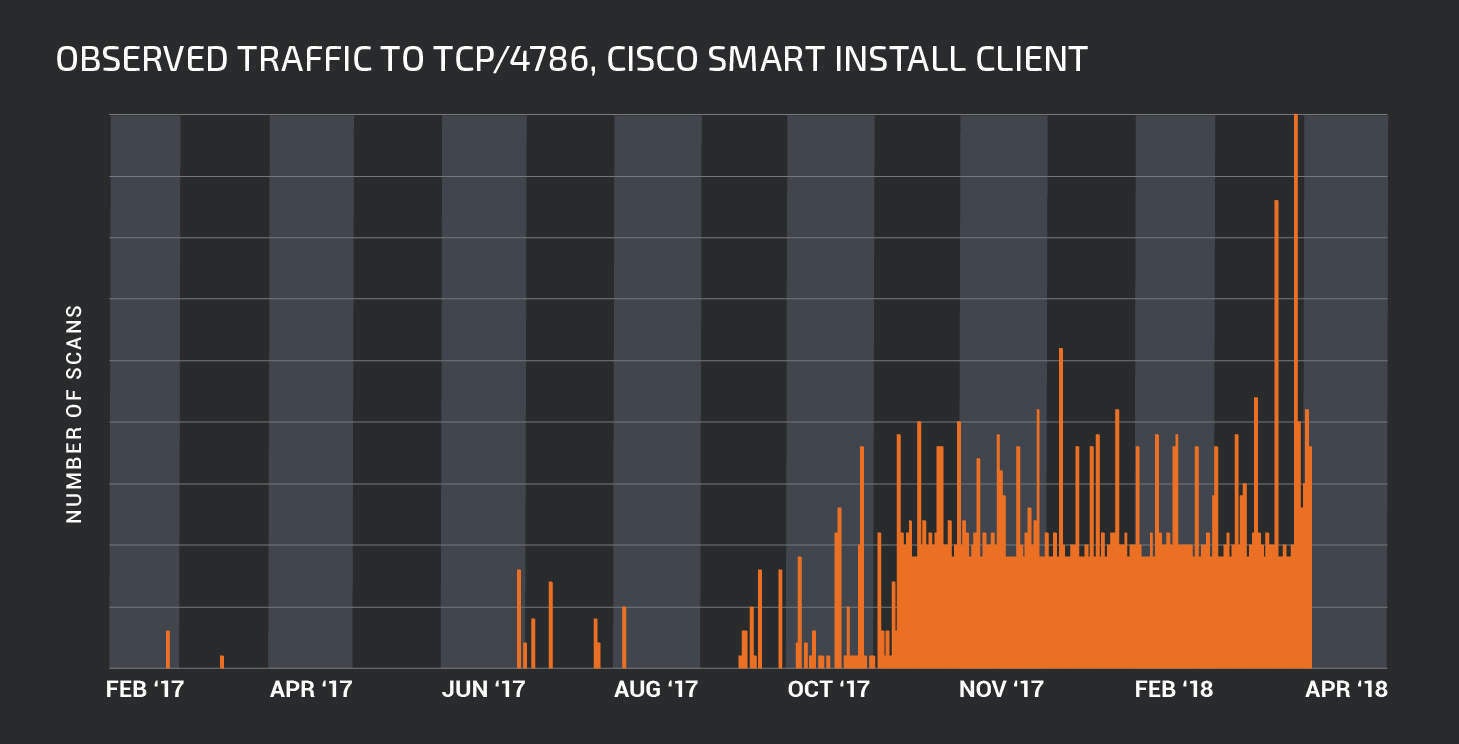
Over the last year, Cisco’s Smart Install tool (SMI), which allows users to remotely access and manage routers, was found to be vulnerable to exploitation by cyber hackers, Cisco said.
While official figures were not released by the government on the scale of the attack, an investigation by Cisco Talos, the security unit of Cisco Systems said more than 168,000 systems could be hit by the attack.
In a blogpost, Cisco wrote:
We began looking at how many devices are potentially vulnerable to this attack. The results were extremely troubling. Using Shodan, [a search engine for specific types of devices] Talos was able to identify that more than 168,000 systems are potentially exposed via the Cisco Smart Install Client.
As a result, Cisco released instructions on how to disable the Smart Install tool on affected devices, and put out an open-source tool for scanning local networks or Internet IP ranges for other SMI-enabled devices.
How to protect against router hacks
Hunton said the routers were an easy target because they are always left on and users rarely have any idea how to update them with anti-virus software.
If I wanted to hack, [a router] is a very good starting point. It’s a device that’s always on. Most people will have them for a long time.
Most people wouldn’t know where to begin in terms of checking their router [for malware] or updating their router or changing their password on their router.
In terms of protecting devices from future hacks, Hunton said updating default passwords and software is a good place to start.
He said:
We need to be a bit more tech savvy. We can’t just bury out heads in the sand and expect the IT experts to do everything for us.
Human error is the most common weakness in cyber-security infrastructure. Hunton said:
It’s like leaving the house and forgetting to lock one of the doors or close one of the windows.
The attacks were allowed to take place after users opened a portal to access their router remotely, using the Cisco software then forget about it and left it open, he said.
It’s people, people are the weakness at the moment. Its about empowering people and making them more aware, giving them some useful and relevant knowledge and insight into how this works.
PwC’s 2015 survey found 50% of the worst breaches that year were caused by inadvertent human error, up from 31% the year before.
Another weakness lies with IT managers who are unable to identify 45% of their organisation’s network traffic, another survey showed.
Almost one in four IT managers were unable to identify 70% of their network traffic, according to a survey by security firm Sophos of 2,700 IT managers.







