
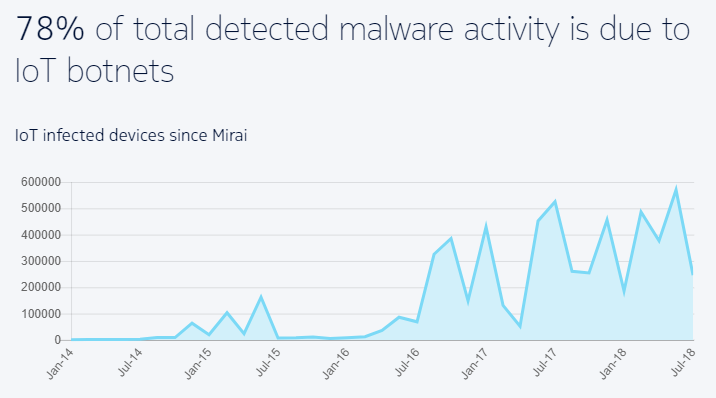
Nokia has discovered a surge in the number of malware botnets within networks over the last two years.
Botnet activity, which is a collection of outsider-controlled devices (bots), on the Internet of Things, the name of the system of electronic devices that connect and share data, now represents 78% of malicious software detections.

Access deeper industry intelligence
Experience unmatched clarity with a single platform that combines unique data, AI, and human expertise.
It is double the rate of IoT botnet activity detected in 2016 when those attacks started in significant numbers.
Bots now make up 16% of infected IoT devices in 2018, while a year ago, only 3.5% of infected devices were being used as IoT bots.
Credit: Nokia

US Tariffs are shifting - will you react or anticipate?
Don’t let policy changes catch you off guard. Stay proactive with real-time data and expert analysis.
By GlobalData5G and larger IoT means more botnets
The danger of malware-infected devices being used as bots is that the attacker can access and control the device, gaining access to private data or using its connection to other devices to build a botnet and take control of other significant devices.
Nokia predicts that botnet malware and other forms of malware used against IoT devices, which can include smart TVs, appliances and cameras, will get worse as consumers accelerate their use of internet-connected equipment, especially with 5G just around the corner.
For example, malware-infected crypto mining is a form of bot activity expected to grow from high-end servers with specialised processors to smartphones and into IoT.
Cybercriminals have smarter tools now to scan for and exploit devices, and they have new tools for spreading malware and bypassing firewalls that cybersecurity experts have to design against.
“The problem with securing hundreds of billions of connected devices is that we must secure hundreds of billions of connected devices.”
Nokia’s Threat Intelligence Lab director Kevin McNamee said: “Cybercriminals are switching gears from the traditional computer and smartphone ecosystems and now targeting the growing number of vulnerable IoT devices that are being deployed.
“You have thousands of IoT device manufacturers wanting to move products fast to market and, unfortunately, security is often an afterthought.”
Cybereason co-founder and chief visionary officer Yossi Naar said: “The problem with securing hundreds of billions of connected devices is that we must secure hundreds of billions of connected devices.
“That may seem obvious and slightly nonsensical, but it is the vast attack surface and the potential complexity of the IoT device security challenge that has us all concerned.”
Infamous botnets since 2016
The Mirai botnet in 2016 was an army of bots based in the US. Attackers scanned the internet for open Telnet ports and then used default passwords to log in and take over routers and IP cameras in the hundreds of thousands.
There was also the Satori IoT malware in 2017 that gave an attacker control over a botnet of 100,000 routers, and, according to Cybereason, the LizardStresser botnet’s creator took over 1,300 internet-enabled cameras to add to an existing botnet of infected machines.







