Security experts have uncovered a new strain of cryptomining malware that employs various evasive techniques to avoid detection.
Cryptomining, also known as cryptojacking, sees malware hijack a device’s computing power to mine for cryptocurrency on behalf of the attacker.
Cybersecurity firm Varonis discovered the new strain – dubbed ‘Norman’ – after it had infected almost every device of a midsize company, causing the performance of its computers to deteriorate.
“Norman seems to be an elaborate cryptominer, more so than the average cryptominer,” said Eric Saraga, security researcher and co-author of the research.
“It tries to hide from analysis, and it uses elaborate techniques to hide itself further. This is not typical behaviour for cryptominers.”
Saraga told Verdict that the business was initially infected a few years ago so it is unknown how it first compromised the computers.
“There are no traces of its origin,” he said.
How Norman hijacks a computer
Norman works in three stages: execution, injection and mining.
It uses the svchost.exe executable – a file used to perform various operations on a computer – to begin the malware’s deployment. Varonis found a Nullsoft Scriptable Install System that contained the various components of the Norman cryptomining malware, among other files.
The malware detects the operating system’s bit type and chooses a different execution path accordingly.
During this stage, the malware injects the main payload, originally named ‘Norman.dll’, which contains the cryptominer.
The malware then uses sophisticated obfuscation tactics to cover its tracks and gets to work, mining the cryptocurrency Monero for the attacker.
To avoid detection, the malware can cease mining when a user opens Task Manager to check why their computer is running slowly. When it’s closed, the malware reinjects the miner.
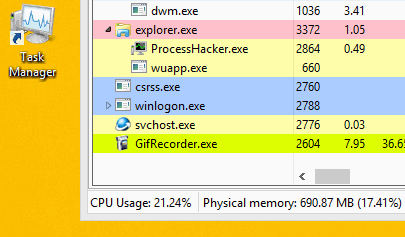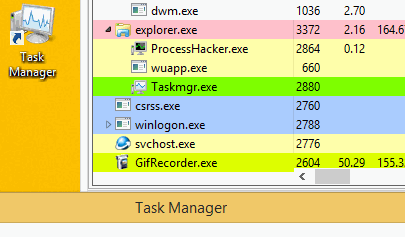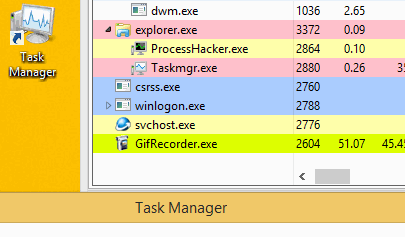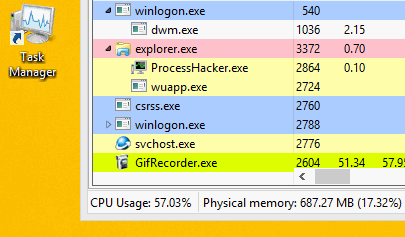
Norman does not have the ability to move around laterally on its own. However, a potentially related PHP shell – a program or script written that lets you execute most commands in browser – discovered on the infected devices could have facilitated this lateral movement.
The findings weren’t conclusive on this, with Sagara explaining that:
“Either the PHP shell is more involved then it appears and infected all the other endpoints, or that an attacker got access to the organization and manually spread the malware. We cannot be sure of anything since there were countless updates and log rotations since the initial infection.”
More technical details about how the cryptoming malware works can be found on Varonis’ blog.
Who is behind Norman?
Varonis’ analysis found that some of the files had comments in French, possibly indicating the location of the perpetrator.
Beyond that it is not possible to determine who is behind it, although Varonis does not believe it is related to a specific criminal hacking group.
“This attack seems more like an above-average attacker trying their luck,” said Saraga.
In 2017, cybercriminals flocked to cryptojacking to take advantage of the then soaring prices of cryptocurrencies such as Bitcoin. But as values of cryptocurrencies dropped, cryptojacking became less profitable and consequently attacks less frequent.
How to defend against cryptominer malware
Varonis provided six tips for businesses to help protect themselves against cryptominers:
- “Use and maintain antivirus and EDR solutions (but don’t let that be your only layer of defense). Endpoint products should be able to detect well-known cryptominers and prevent infections before any damages occur. Keep in mind that new variants or new evasion techniques can bypass endpoint security products.
- Keep all operating systems up to date. Patch management is crucial to prevent exploitations and unwanted infections.
- Monitor network traffic and web proxies. It is possible to detect and prevent a portion of attacks by blocking traffic based on malicious domains or restricting unnecessary communications.
- Monitor CPU activity on computers. Cryptominers generally use the computer’s CPU to mine. Any noticeable degradation in processing speed requires investigation.
- Monitor DNS for unusual use of dynamic DNS services (like DuckDNS). While DuckDNS and other dynamic DNS services play a legitimate role, malware’s use of DuckDNS made it easier for our teams to detect infected hosts in this investigation.
- Have an IR plan ready – Make sure you have the right procedures for similar incidents, and be capable of automatically detecting, containing, and remediating cryptominers.”
Read more: LoudMiner uses virtualisation software in an “unusual case” of cryptojacking