
A prolific scamming group dubbed London Blue is now targeting business employees in Asia and using spoofed email addresses to trick businesses into handing over cash.
London Blue operates a sprawling scamming operation out of West Africa, with the majority of its scams originating from Nigeria.
They employ a largely unsophisticated technique known as ‘business email compromise’ (BEC), in which the scammers impersonate a high-ranking employee and ask for funds to be transferred to a bogus account.
Cybersecurity firm Agari has been monitoring the group since its chief financial officer was sent a scam email in August last year by London Blue.
In December, Agari revealed how London Blue possessed a master list of contact details for 50,000 professionals around the world to target with its BEC campaigns. The majority were chief financial officers.
Now, Agari says that the group has added an extra 8,500 employees to that list, spanning across 7,800 companies around the world.
These lists are acquired through legitimate marketing lead firms, says Crane Hassold, senior director of Threat Research at Agari.
He says the lists are “fascinatingly easy” to refine by “geographical region, employees, company size”.
To check the employee still works for the company they send out test emails. Those that bounce are no longer at the company and therefore no longer of value to the scammers.
Opening up to new markets in Asia
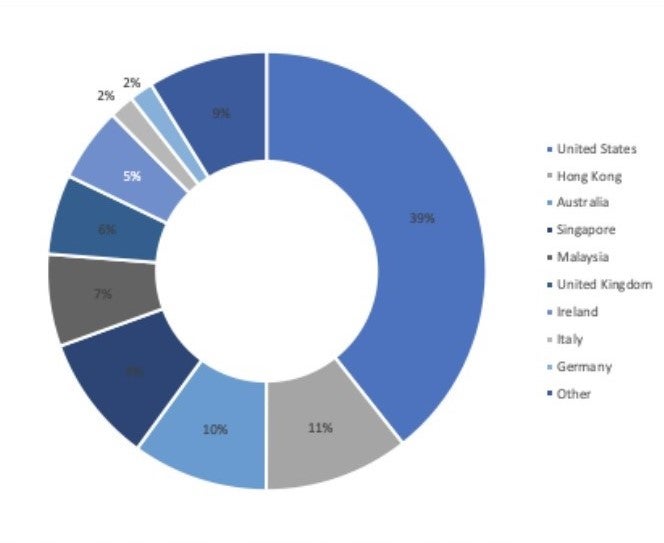
The majority of London Blue’s targets are located in the US. But over the last five months, Agari has observed a shift towards targeting employees located in Asia who are working for non-Asian companies.
“This makes sense since the BEC emails we have observed targeting individuals in these countries are written in English and not in the local language,” Agari’s latest report states.
In February, London Blue launched a BEC campaign against targets in Hong Kong and Singapore, while in March the group targeted employees located in Malaysia.
Asian countries now make up around a quarter of London Blue’s BEC targets.
London Blue turns on the spoof
Traditionally, London Blue has used a temporary email account with a fake display name to carry out its BEC email campaigns.
In late-February, the group shifted to spoofing email addresses, a common technique used by scammers in which the email header is forged to hide the original source of the email.
Spoofed emails are usually flagged as malicious, but Agari says that most of the companies targeted by London Blue’s spoofed email addresses do not have a DMARC record, a simple tool that can catch spoofed emails.
Agari passes all of its findings on to law enforcement, but catching the scammers is difficult.
“There needs to be a confirmed victim before action can be made by law enforcement,” says Hassold, an 11 year veteran of the FBI.
Hassold worries that in the future the more organised hacking groups in Eastern Europe will realise the profitability of BEC and launch more sophisticated campaigns of their own.
Read more: Scarlet Widow: The romance scam group preying on the disabled and divorced







