The technology industry continues to be a hotbed of patent innovation. Activity is driven by the escalating need for robust security measures in areas such as IoT, hardware authentication, and secure key storage, as well as the increasing awareness of PUFs’ resistance to attacks, and growing importance of technologies such as semiconductor manufacturing processes, PUF circuit designs, and cryptographic algorithms, collectively driving advancements in PUF-based cybersecurity solutions. In the last three years alone, there have been over 1.5 million patents filed and granted in the technology industry, according to GlobalData’s report on Cybersecurity in technology: physically unclonable functions (PUFs). Buy the report here.

Access deeper industry intelligence
Experience unmatched clarity with a single platform that combines unique data, AI, and human expertise.
However, not all innovations are equal and nor do they follow a constant upward trend. Instead, their evolution takes the form of an S-shaped curve that reflects their typical lifecycle from early emergence to accelerating adoption, before finally stabilizing and reaching maturity.
Identifying where a particular innovation is on this journey, especially those that are in the emerging and accelerating stages, is essential for understanding their current level of adoption and the likely future trajectory and impact they will have.
185+ innovations will shape the technology industry
According to GlobalData’s Technology Foresights, which plots the S-curve for the technology industry using innovation intensity models built on over 1.6 million patents, there are 185+ innovation areas that will shape the future of the industry.
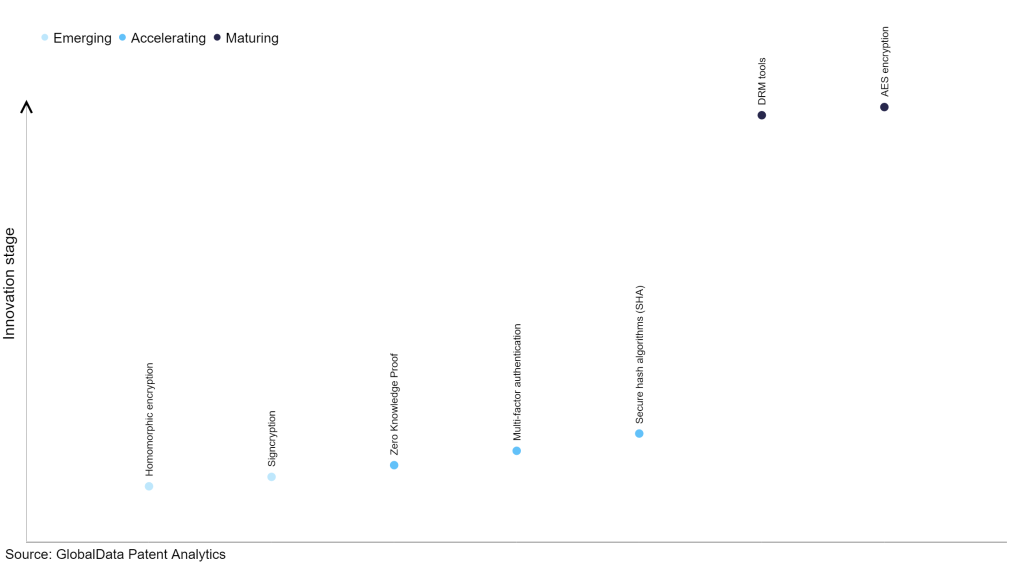
Within the emerging innovation stage, homomorphic encryption and signcryption are disruptive technologies that are in the early stages of application and should be tracked closely. Zero knowledge proof, multi-factor authentication and secure hash algorithms (SHA) are some of the accelerating innovation areas, where adoption has been steadily increasing. Among maturing innovation areas are DRM tools and AES encryption, which are now well established in the industry.
Innovation S-curve for cybersecurity in the technology industry
Physically unclonable functions (PUFs) is a key innovation area in cybersecurity
Physically uncloneable functions (PUFs) represent a security technology employing distinctive physical attributes of devices to establish authentication. By generating a response to a challenge rooted in the device's singular physical traits influenced by manufacturing differences, PUFs ensure the device cannot be replicated, thus enabling secure authentication.
GlobalData’s analysis also uncovers the companies at the forefront of each innovation area and assesses the potential reach and impact of their patenting activity across different applications and geographies. According to GlobalData, there are 180+ companies, spanning technology vendors, established technology companies, and up-and-coming start-ups engaged in the development and application of physically unclonable functions (PUFs).
Key players in physically unclonable functions (PUFs) – a disruptive innovation in the technology industry
‘Application diversity’ measures the number of applications identified for each patent. It broadly splits companies into either ‘niche’ or ‘diversified’ innovators.
‘Geographic reach’ refers to the number of countries each patent is registered in. It reflects the breadth of geographic application intended, ranging from ‘global’ to ‘local’.
Among the companies innovating in physically unclonable functions, Intel is the leading patent filer. The company’s patents are aimed at a method for securely providing secret keys in the manufacturing of integrated circuits through fuse attestation. An apparatus is outlined, comprising elements such as a storage location, a physically unclonable function (PUF) circuit, a PUF key generator, an encryption unit, and multiple fuses. These components work in tandem. The PUF circuit generates a unique value, the PUF key generator processes it into a PUF key, and the encryption unit encrypts a configuration fuse value. Both the PUF key and the configuration fuse value are sent to a key server. Upon confirming that the configuration fuse value designates the apparatus as a production component, the key server furnishes a fuse key to be stored in the array of fuses.
Other prominent patent filers in the space include International Business Machines (IBM) and Mitsubishi Electric.
In terms of application diversity, Intel held the top position, while E. Merck and Mitsubishi Electric stood in second and third positions, respectively. By means of geographical reach, E. Merck leads the pack, followed by eMemory Technology and Visa.
PUFs play a critical role in cybersecurity by leveraging the unique physical properties of hardware components to generate cryptographic keys or identifiers. These keys are virtually impossible to duplicate, providing an exceptionally robust defence against unauthorized access, counterfeiting, and attacks on sensitive information, thereby fortifying the security of various systems and applications.
To further understand the key themes and technologies disrupting the technology industry, access GlobalData’s latest thematic research report on Cybersecurity.
Data Insights
From

The gold standard of business intelligence.
Blending expert knowledge with cutting-edge technology, GlobalData’s unrivalled proprietary data will enable you to decode what’s happening in your market. You can make better informed decisions and gain a future-proof advantage over your competitors.







