The technology industry continues to be a hotbed of innovation, with activity driven by the increasing cybersecurity threats, regulatory compliance requirements, and the growing adoption of cloud-based services, as well as growing importance of technologies such as advanced encryption algorithms, digital certificates, secure key exchange mechanisms, and secure communication protocols. These technologies bolster cybersecurity defences by providing robust authentication measures, safeguarding sensitive information, and preserving the integrity of digital interactions. In the last three years alone, there have been over 3.6 million patents filed and granted in the technology industry, according to GlobalData’s report on Innovation in Cybersecurity: Mutual authentication protocols. Buy the report here.
However, not all innovations are equal and nor do they follow a constant upward trend. Instead, their evolution takes the form of an S-shaped curve that reflects their typical lifecycle from early emergence to accelerating adoption, before finally stabilising and reaching maturity.
Identifying where a particular innovation is on this journey, especially those that are in the emerging and accelerating stages, is essential for understanding their current level of adoption and the likely future trajectory and impact they will have.
300+ innovations will shape the technology industry
According to GlobalData’s Technology Foresights, which plots the S-curve for the technology industry using innovation intensity models built on over 2.5 million patents, there are 300+ innovation areas that will shape the future of the industry.
Within the emerging innovation stage, byzantine fault tolerant blockchain, secure multi-party computing, and decentralised identity framework are disruptive technologies that are in the early stages of application and should be tracked closely. Secure hash algorithms (SHA), zero knowledge proof, and private blockchains are some of the accelerating innovation areas, where adoption has been steadily increasing. Among maturing innovation areas are firmware security and multimedia signal encryption, which are now well established in the industry.
Innovation S-curve for cybersecurity in the technology industry
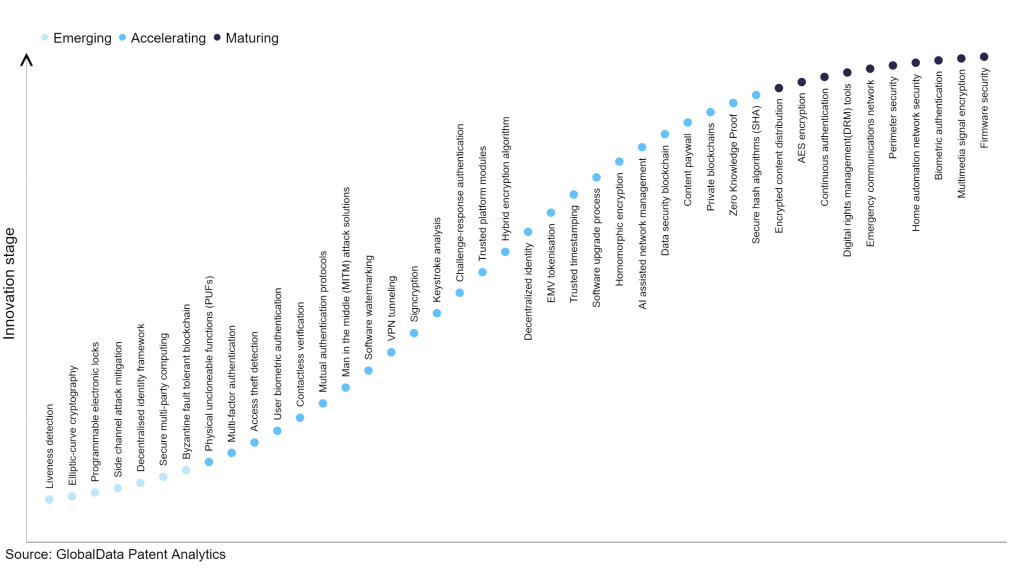
Mutual authentication protocols is a key innovation area in cybersecurity
Mutual authentication protocols are vital security mechanisms that allow two entities to validate each other's identities prior to initiating any form of communication or transaction. This authentication process serves as a crucial safeguard against unauthorised access and malicious entities attempting to compromise sensitive information. Mutual authentication protocols find application across various scenarios, including remote access, secure file transfers, and secure web browsing, among others, ensuring the integrity and confidentiality of data exchanges in diverse contexts.
GlobalData’s analysis also uncovers the companies at the forefront of each innovation area and assesses the potential reach and impact of their patenting activity across different applications and geographies. According to GlobalData, there are 250+ companies, spanning technology vendors, established technology companies, and up-and-coming start-ups engaged in the development and application of mutual authentication protocols.
Key players in mutual authentication protocols – a disruptive innovation in the technology industry
‘Application diversity’ measures the number of different applications identified for each relevant patent and broadly splits companies into either ‘niche’ or ‘diversified’ innovators.
‘Geographic reach’ refers to the number of different countries each relevant patent is registered in and reflects the breadth of geographic application intended, ranging from ‘global’ to ‘local’.
Patent volumes related to mutual authentication protocols
Source: GlobalData Patent Analytics
Sony Group is a leading patent filer in mutual authentication protocols. The company’s patents are aimed at invention describing a data transmitting apparatus in which a device information obtaining unit obtains device information of a device connected to the data transmitting apparatus. A verification unit verifies the validity of a data receiving apparatus, based on the device information obtained by the device information obtaining unit, and a control unit performs control as to whether to obtain the device information through a wireless communication unit or obtain the device information through a wire communication unit.
The control unit also determines whether to transmit image information encrypted by a first encryption unit from the wireless communication unit or transmit image information encrypted by a second encryption unit from the wire communication unit when the verification unit verifies that the data receiving apparatus is authorised.
Other prominent patent filers in the space include Huawei and Qualcomm.
By geographic reach, Novastone Media leads the pack, followed by Anect and YouView TV. In terms of application diversity, KB Financial Group holds the top position, followed by Shinhan Financial Group and American Virtual Cloud Technologies.
Mutual authentication protocols have revolutionised the way entities authenticate and verify each other's identities. Mutual authentication protocols enhance the security of communication channels by requiring both parties to prove their authenticity before establishing a connection.
By implementing innovative mutual authentication protocols, organisations can establish secure and trustworthy connections, safeguard sensitive information, and mitigate the risks associated with malicious entities attempting to exploit vulnerabilities in the authentication process.
To further understand how cybersecurity is disrupting the technology industry, access GlobalData’s latest thematic research report on Cybersecurity – Thematic Research.
Data Insights
From

The gold standard of business intelligence.
Blending expert knowledge with cutting-edge technology, GlobalData’s unrivalled proprietary data will enable you to decode what’s happening in your market. You can make better informed decisions and gain a future-proof advantage over your competitors.







