The technology industry continues to be a hotbed of patent innovation. Activity is driven by the growing frequency and sophistication of cyber threats, coupled with the widespread adoption of online transactions and the increasing use of IoT devices, and growing importance of technologies such as encryption protocols and secure authentication methods. In the last three years alone, there have been over 1.5 million patents filed and granted in the technology industry, according to GlobalData’s report on Cybersecurity in technology: MITM attack mitigation. Buy the report here.
However, not all innovations are equal and nor do they follow a constant upward trend. Instead, their evolution takes the form of an S-shaped curve that reflects their typical lifecycle from early emergence to accelerating adoption, before finally stabilizing and reaching maturity.
Identifying where a particular innovation is on this journey, especially those that are in the emerging and accelerating stages, is essential for understanding their current level of adoption and the likely future trajectory and impact they will have.
185+ innovations will shape the technology industry
According to GlobalData’s Technology Foresights, which plots the S-curve for the technology industry using innovation intensity models built on over 1.6 million patents, there are 185+ innovation areas that will shape the future of the industry.
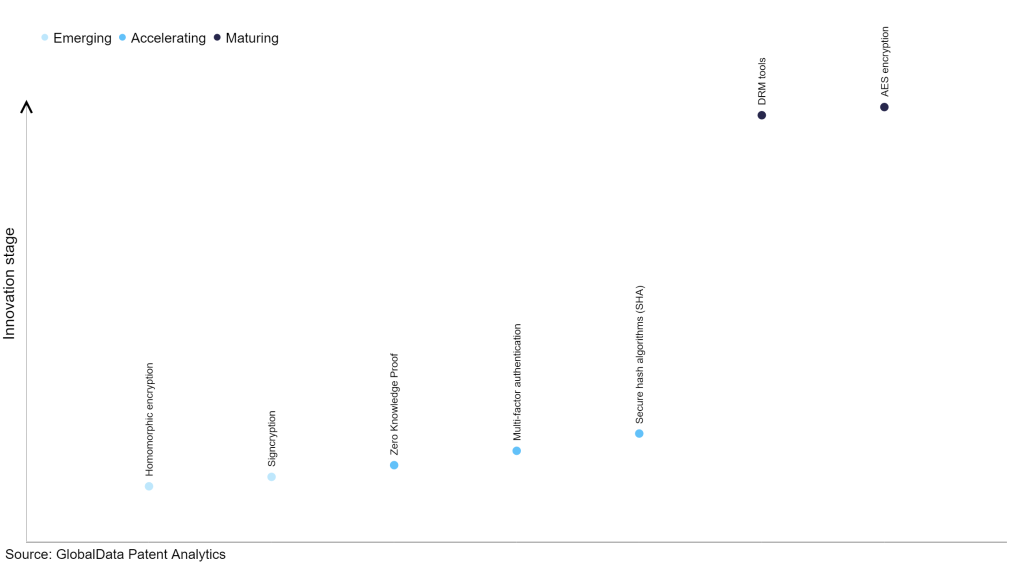
Within the emerging innovation stage, homomorphic encryption and signcryption are disruptive technologies that are in the early stages of application and should be tracked closely. Zero knowledge proof, multi-factor authentication and secure hash algorithms (SHA) are some of the accelerating innovation areas, where adoption has been steadily increasing. Among maturing innovation areas are DRM tools and AES encryption, which are now well established in the industry.
Innovation S-curve for cybersecurity in the technology industry
MITM attack mitigation is a key innovation area in cybersecurity
Mitigating Man-In-The-Middle (MITM) attacks involves employing methods and technologies to thwart or identify malicious efforts to intercept sensitive information exchanged between multiple parties. This includes confidential data such as usernames, passwords, financial details, and other private information. These illicit activities are typically orchestrated by cybercriminals with intentions of theft, manipulation, or corruption for personal gain, and can result in severe consequences for individuals, businesses, and organizations.
GlobalData’s analysis also uncovers the companies at the forefront of each innovation area and assesses the potential reach and impact of their patenting activity across different applications and geographies. According to GlobalData, there are 3,580+ companies, spanning technology vendors, established technology companies, and up-and-coming start-ups engaged in the development and application of MITM attack mitigation.
Key players in MITM attack mitigation – a disruptive innovation in the technology industry
‘Application diversity’ measures the number of applications identified for each patent. It broadly splits companies into either ‘niche’ or ‘diversified’ innovators.
‘Geographic reach’ refers to the number of countries each patent is registered in. It reflects the breadth of geographic application intended, ranging from ‘global’ to ‘local’.
Patent volumes related to MITM attack mitigation
Source: GlobalData Patent Analytics
Among the companies innovating in MITM attack mitigation, Microsoft is one of the leading patents filers. The company’s patents are aimed at establishing a data protection service that involves several steps. Initially, a request to set up a first tenant from a group of tenants managed by a single data protection service is received. Here, a tenant refers to one entity among several. This unified data protection service caters to all tenants within the group. The first encryption key, which is exclusive to the first tenant and enables the decryption of their data in the data store, is securely stored. This key, however, cannot be employed to decrypt data of other tenants from the same data store. Instead, each tenant in the group has a unique encryption key associated with them, ensuring that it can only be used to decrypt their specific data on an individual tenant basis. Other prominent patent filers in the space include International Business Machines (IBM) and Huawei.
In terms of application diversity, Huawei leads the pack, while Qualcomm and Telefonaktiebolaget LM Ericsson are in second and third positions, respectively. By means of geographic reach, Visa held the top position, followed by Qualcomm and InterDigital.
MitM attacks pose a significant threat to the confidentiality and integrity of sensitive information exchanged online. By implementing robust MitM attack mitigation measures, organizations and individuals can ensure that their data remains secure and inaccessible to unauthorized parties. This is especially crucial in industries such as finance, healthcare, and e-commerce, where protecting sensitive information is paramount. MitM attack mitigation not only safeguards against potential breaches, but also fosters trust and confidence in digital interactions, ultimately contributing to a more secure and resilient digital ecosystem.
To further understand the key themes and technologies disrupting the technology industry, access GlobalData’s latest thematic research report on Cybersecurity.
Data Insights
From

The gold standard of business intelligence.
Blending expert knowledge with cutting-edge technology, GlobalData’s unrivalled proprietary data will enable you to decode what’s happening in your market. You can make better informed decisions and gain a future-proof advantage over your competitors.