
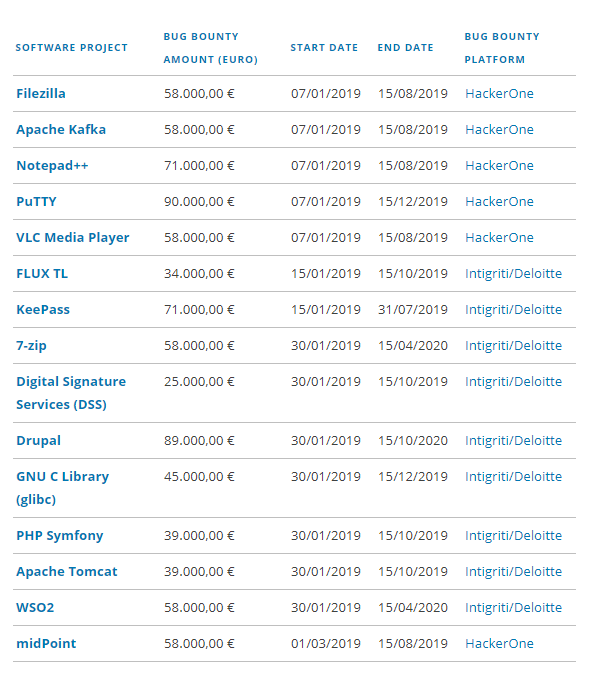
The targets have been set for bounty hunters to search out vulnerabilities in the open source software used across European Union institutions, starting from 7 January 2019.
The European Commission has employed security platforms HackerOne and Intigriti to source and manage the bug bounty hunters or hackers who will find potential threats in 14 free software projects used by the EU.

Access deeper industry intelligence
Experience unmatched clarity with a single platform that combines unique data, AI, and human expertise.
MEP Julia Reda said in a blog that these are projects which “EU institutions rely on” and were chosen by candidates from inventories and in a survey.
“The amount of the bounty depends on the severity of the issue uncovered and the relative importance of the software,” she said.
Credit: juliareda.eu

US Tariffs are shifting - will you react or anticipate?
Don’t let policy changes catch you off guard. Stay proactive with real-time data and expert analysis.
By GlobalDataVeracode: Automation can do it better than an army of hackers
But Paul Farrington, Director of EMEA and APJ at Veracode, an American application security company, says: “The fact that the EU wants to address the state of open source software security is a good thing. Bug Bounty programs are a good thing too, but they are really the ‘final mile’ in a long journey.
“You can’t rely on detecting the majority of vulnerabilities by employing an army of people to do what automation does better.
“Some of the projects in scope for the EU testing, today rely on other open source projects that are already known to have vulnerabilities associated with them. A simple ‘software composition analysis’ scan of these projects, would reveal the use of such insecure libraries.”
Farrington adds: “We need humans to detect vulnerabilities that computers today struggle to identify.
“That said, there’s really much that could be done to improve the general hygiene of software development using modern scan automation.”
Rise of the cyber bounty hunters
According to Farrington, there has been an explosion in the popularity of bug bounty programs and organisations need to provide more ways for ethical hackers to responsibly disclose vulnerabilities and bugs.
He says: “For too long, security researchers have risked being penalised for good intentions, as they report potential vulnerabilities to commercial software publishers.
“In the open source arena, it’s a common misconception that somebody else in the community is looking for the security defect. In practice, open source software is really no more secure than proprietary software.”
HackerOne connects bounty hunters to the EC
Verdict Encrypt talked to HackerOne security engineer Laurie Mercer about how the hacker-powered security platform connects companies and ethical hackers to catch cyber vulnerabilities.
“The researchers essentially will find vulnerabilities in the assets of the customers and report them in a structured way through our marketplace. And in return the customers will pay them money, which is what we call a bounty,” said Mercer.
It offers bounties to hackers from around the world and connects them with companies and organisations like the European Commission.
The hackers are paid individually, but the organisations who use their services agree a fixed pot at the start of the bounty programme that HackerOne manages and issues to successful hackers in their currency of choice – dollars, rupees, euros or even Bitcoin.







